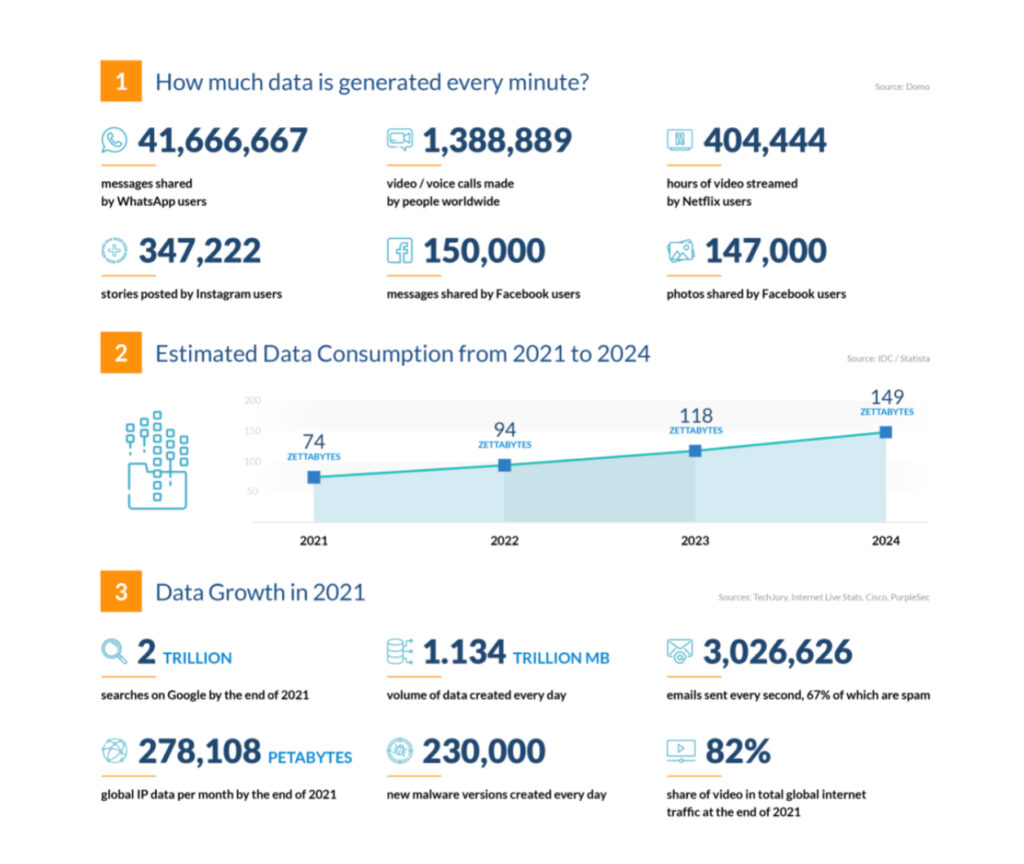
It is almost impossible to ignore the way the world has jumped from paper-based, siloed and manual record-keeping to digitised, interconnected and automated systems. This game-changing shift has led to the production, storage and consumption of over 300 zetabytes of data in the last 10 years alone, exponentially more than in the previous century as a whole.
Just like all property, a perceived value people attach to an item presents a need for its protection from known, unknown and potential harm.
Cybersecurity
From this point of view, cybersecurity can be described as the collective effort to safeguard systems and assets held online and any others kept in digital platforms.
Cybercrime
Cyber-attacks can therefore be viewed as any attempts to access or manipulate a set of digital property which one doesn’t own or have permission to access. In an environment with a supporting legal framework for online activity, this is what’s known as cybercrime: typically traced back to a machine acting on behalf of a human.
The COVID-19 pandemic has seen a 600% worldwide surge in cybercrime related incidents, a concerning trend almost as chaotic as the 2020-2021 global shocks seen in logistics and supply-chain industries.
Typical cybercrimes involve:
Social engineering, where creative language is used to trigger impulsive behaviour that’s usually used to get hidden access a person’s financial records or control of ICT devices. With either one of these, a person can be held at ransom or have their data harvested for a number of lucrative opportunities online. A 2021 African cybersecurity report had social engineering as the leading cybercrime on the continent, with the most successful type being fraudulent investment opportunities distributed via email and social media.
Other leading African cybercrimes in 2021 were hacked accounts and viral software. Both cases can involve:
· Identity theft, where deceptive methods are used to gain access to a person or organisation’s private and (usually) sensitive data. The University of Zimbabwe is reported to have had a first-hand account of this through an online accommodation system hack that netted the cyber-intruder US$ 3,000 in a month-long escapade;
· Email phishing, where millions of email addresses can receive an almost identical email embedded with malicious software. A simple click on the bait and a victim will be hooked by an online scam. An example close to home is TM Pick n Pay’s ZWL 22 million reported to have been fleeced via email.
What’s new in Zimbabwe’s cyberspace?
If it feels like you’re seeing cyber security issues in the news almost every single day, it’s because you almost certainly are. Research shows that cyber-attacks occur at a rate of around one every 39 seconds and these attacks are indiscriminate. What this means is simple: if you have an internet-connected device, you are vulnerable. This should be of real concern to both individuals and businesses.
When it comes to legal support, Zimbabwe is fairly new to the scene. Until as recently as December 2021, people and companies had no framework in place to pursue compensation for losses resulting from cybercrimes in the country. Through Zimbabwe’s (2021) Data Protection Act, a firmer foundation is in place to complement a host of anti-viral software and data protection practices cybersecurity experts recommend worldwide.
Considering recent and anticipated cybersecurity threats, the Act covers cybersecurity at a personal and organisational level, with a range of measures addressing commercial and non-commercial spaces – including social media.
DataReportal estimates that 5.01 million of Zimbabwe’s 14 million+ population were internet users in 2021, a massive dataset exposed to various forms of cybercrimes – more so with the interconnected nature of the modern cyberspace.
The value of Zimbabwe’s online data
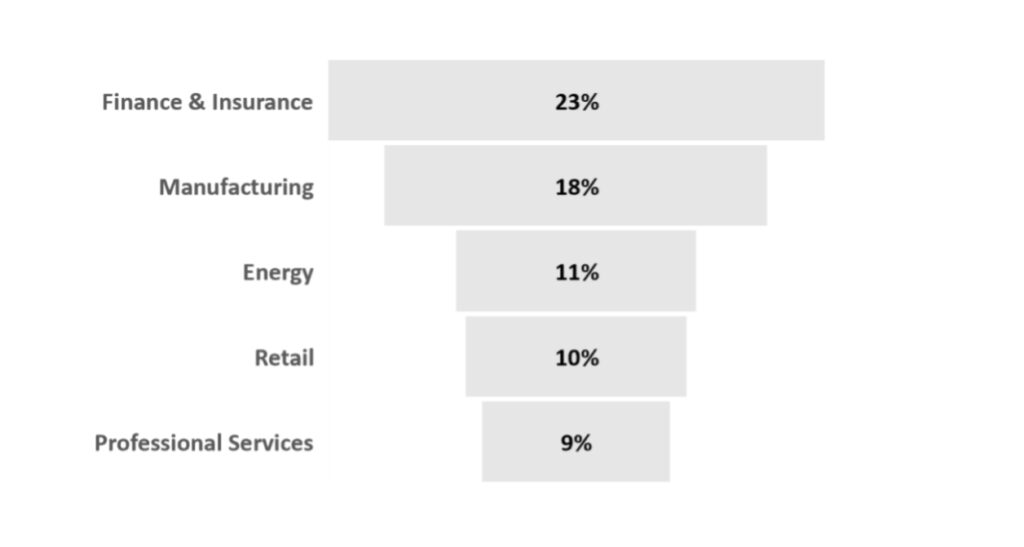
In finance, one of the world’s most targeted cybercrime industries, the latest Reserve Bank of Zimbabwe National Payment System data highlights a 42% spike in the value of (local) online transactions from ZWL 2.08 trillion to ZWL 2.96 trillion, an increase realised between September-December 2021.
For all intermediaries in the country’s financial space, the appeal of fee and commission incomes brings with it a burden of securing transactions and the tonnes of associated individual and company data from prying eyes in the cyberspace.
Cybersecurity investment
According to CISCO, the average annual cybersecurity spend of large enterprises around the world is US$ 1 million, a figure that may seem high but is necessary considering an average data breach cost of US$ 4.25 million to such organisations. But as a benchmark to avoid feeling priced-out, IBM recommends a 9%-14% annual IT department budget as a good entry point to cybersecurity for a company.
With improving financial sector inclusion in Zimbabwe as well as adoption of and participation in various internet-based platforms, the need for data literacy and cyber-risk aversion has shot-up.
Given the number of cyber security threats that exist and the potential consequences – which can include loss of data and even complete loss of customer trust – adopting measures to
protect your business is, now more than ever, beyond essential. For this reason, it is critical that businesses work with a professional IT support company to protect their data and systems.
Sign-up for the Dandemutande’s cybersecurity webinar via Zoom at 11am on Thursday 10 March 2022, for expert insights and opinions on:
· Zimbabwe’s cyberspace developments
· Data protection industry best-practices
· Cloud-based infrastructure protection solutions and
· The best ways to safeguard intellectual property in Zimbabwe
Dandemutande is an innovative, fast-growing ICT solutions provider and recipient of the Institute of Cyber Security Zimbabwe – Best Cyber Security Company of the Year Award 2021.



Leave A Comment